Over the past 18 months, the pandemic has forced many of us out of our offices. Governments around the world encouraged us to work from home where possible. With restrictions easing in many parts of the world – including the UK and the US – hybrid working seems set to become the post-COVID norm. IDC agrees, predicting that by 2023 60% of data will be generated by homeworkers.
But home-working during the pandemic wasn’t without risk. And longer-term plans for hybrid working need careful evaluation if they are to succeed without giving cybercriminals an easy backdoor into corporate systems. Cybersecurity attacks increased during the pandemic, with a 485% rise in ransomware attacks alone between 2019 and 2020.
One reason could be that we were simply spending more time at home and – with cinemas, retail outlets, gyms and pretty much every leisure activity closed – we generally had more spare time, and consequently, spent more time online.
The perfect storm
Cyberattacks also increased because many remote workers altered firewall settings and access points to connect to Software-as-a-Service (SaaS-based) work systems from their homes – everything from Office365 to remote call centre solutions and specialist software for accounting, supply chain management, and payroll.
The rapid adoption of these SaaS-based solutions enabled businesses to respond quickly to work-from-home guidance. And there’s no doubt the quick pivot they offered saved jobs, protected companies from collapse, and played an essential role in helping employees observe lockdown and social distancing rules. The global economy would be in a very different place today if these solutions didn’t exist.
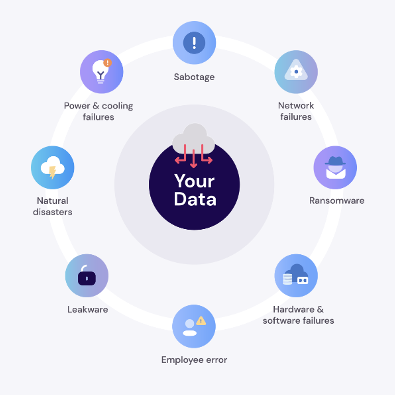
But it also meant that, for the first time, most data was being produced outside of the corporate firewall and no longer saved on physical on-premises hardware. This led to a spike in ransomware attacks – not just on corporate IT systems but against the very SaaS-based applications supporting workers during the pandemic.
Despite the general security of these applications, hackers found more and more ingenious ways to gain access through an end user’s compromised operating system. This allowed them to attack the cloud services themselves. As such, end-users of SaaS solutions now need to be ever more vigilant, and follow IT and security best-practice – including regularly changing their passwords, not storing unencrypted lists of passwords, and keeping antivirus software updated.
Although working remotely, IT teams also have an ongoing role in ensuring remote workers don’t stop following corporate IT security policies. The key takeaway is that SaaS adoption does not, unfortunately, allow us to relax our IT security posture.
Who’s responsible for protecting data?
The challenges go much deeper than this, however. Many companies assumed that because they’d migrated to SaaS-based applications, they didn’t need to worry about backing up the data with the same diligence as they would have done with more traditional on-premises applications. There was – and to an extent still tends to be – the assumption that SaaS providers are entirely responsible for looking after the data produced by their applications.
This is important because SaaS vendors are only responsible for data availability and not data recovery, so if a ransomware attack happens on their watch and the data gets wiped, they’re not liable for recovering it. Some cloud providers – such as Microsoft and AWS – have a shared responsibility model for data: they’ll take responsibility for some of it, but users have to take charge of the rest.
For these reasons, a comprehensive data protection and disaster recovery system is still so important.
The data stored on SaaS platforms needs to align with existing data backup and recovery SLAs within the organisations that have deployed them. Ransomware attacks can lock out access to data and ultimately wipe the information completely. So, it’s vital that companies using SaaS-based solutions backup the data independently of the service providers, and in line with corporate policy.
Businesses mustn’t take a more relaxed approach to disaster recovery because they’ve adopted SaaS-based solutions. In fact, the potential complexity of SaaS adoption – especially if it’s across multiple cloud environments and with uptake amongst a large proportion of remote workers – means that it’s critical to have a tried, tested, and regularly updated DR strategy in place.
This will ensure businesses can continue to benefit from the ease of deployment promised by SaaS solutions without falling victim to the growing number of ransomware attacks.
Originally published on the Commvault blog, by Jonathan Bowl, August 3, 2021.
