If a midsize company decides to pay after a ransomware attack, chances are it’s not getting all of its encrypted data back, according to a session at this week’s Gartner’s Security & Risk Management Summit.
“What we see is that about 4% of the data is non-recoverable,” said Paul Furtado, a senior director and analyst of MSE security at Gartner. Furtado led the “Fighting Ransomware in Midsize Enterprises” session. “So that means, yes, you paid, and yes, you got a decryption key, but these bad actors don’t care about what is happening to your data when they go through the encryption.”
There may be other issues with data targeted by ransomware, as well: “Think of a database where somebody may have records open or a file in use,” he said. “They’re going to encrypt that data, even though it’s not necessarily sitting at rest and may be sitting in transit. But the chances are when you go to decrypt it, it’s corrupted.”
Gartner identifies midsize enterprises as companies with between 100 and 1,000 employees, and with revenues between $50 million and $1 billion. Furtado notes that most midsize companies have an IT budget of less than $20 million, fewer than 30 people in the IT departments and more than 50% of such companies “don’t even have a dedicated cybersecurity leader.”
So, how can a company determine how to respond to a ransomware attack?
“The answer is: it depends!” Furtado said. “It really is unique to you, your ability to recover, the impact to the business. You need to decide if it’s worthwhile paying to get that decryption key, or should you try to recover from backups and other tools you may have available.”
He notes that law enforcement recommends that companies do not pay and that payment should be a last resort. If one does decide to pay, however, he explained that the average cost of a ransomware payment in Q1 2020 was $178,254 — and the costs in downtime following the ransomware attack can be five to 10 times the actual ransom amount. That $178,254 figure represents a dramatic rise from a $5,593 average payment in Q3 2018. And as for the ransomware threat level, it increased by 148% in March over the previous month.
The session also touched on primary ransomware payloads — spear phishing, remote desktop connection compromise, and malware wrappers — as well as deployment timelines (in 76% of ransomware cases, ransomware was deployed outside of working hours), how much data is sold for and more.
According to Furtado, midsize enterprises can protect themselves from today’s ransomware threat by taking the following steps:
- Conduct better awareness training: Offer smaller sessions over time, rather than a single one-hour session that employees attend once every 12 months.
- Ensure that email spam filters implement URL protection: An organization’s spam filters should also use email/attachment sandboxing, endpoint protection that implements non-signature technologies, and better web filtering (including enabling gateway antivirus, blocking risky file extensions, using HTTPS filtering, and blocking unnecessary ports).
- Close open doors: Block unnecessary ports on endpoints, for example.
- Adhere to the “3-2-1” rule for backups: Keep three copies of your data on two different media types, with one being offsite.
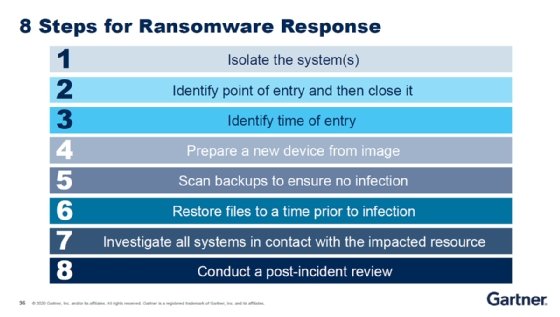
One of the closing parts of the presentation included an eight-step ransomware response plan, which can be seen below:
Originally published on TechTarget by
Alexander Culafi, September 17, 2020.
