by Christine Thome | Jul 3, 2018 | mobile threats, Security
Chances are you’d be more inclined to open and act on an email from a colleague, friend or someone you know as opposed to someone you don’t. Cybercriminals know this, which is why they are sending attacks to your friends and colleagues—from your email account....
by Christine Thome | Jun 27, 2018 | Networking
There’s no question that Cisco is the big dog when it comes to network solutions. But like a regal and older Great Dane, Cisco tends to be content with the large dish of customers in front of them, deciding to conserve their energy instead of spending it on...
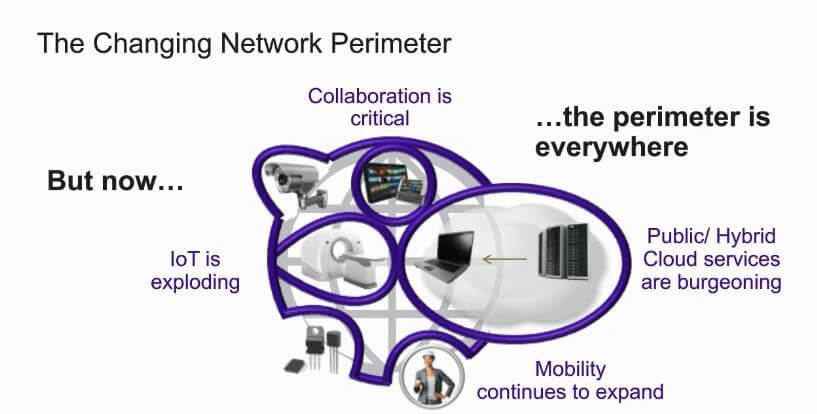
by Christine Thome | Jun 6, 2018 | Networking, Security
The digitalization of our society is happening now, uniquely and definitively transforming how organizations operate on a day-to-day basis, and opening up progressive and exciting opportunities across all industries. Some of these include: In hotel and lodging, mobile...
by Christine Thome | Jun 6, 2018 | Backup, Security, Storage
Along with most everyone rushing to update their privacy policies and reaffirm your consent, the “other” copies of your data have begun to creep into the discussion, such as a piece that appeared on The Register. Wait? What other copies?!? You know, all...
by Paul Comfort | Jun 6, 2018 | Cloud, Infrastructure, Security
Security is hard, and here is a great example as to why. I am using Amazon WorkSpaces for this example because I recently ran up against this problem, but a similar issue could happen during any cloud software product’s normal lifecycle. Amazon WorkSpaces is a...

by Christine Thome | Jun 5, 2018 | Uncategorized
Although many industries have long offered product warranties to assure customers the products they purchase will function as advertised, this has not been true for cybersecurity. When a security product fails, customers have had little recourse — until now....
by Christine Thome | May 25, 2018 | Uncategorized
Most of Chi’s customers live in the United States and are not subject to GDPR. However, some of our customers operate multi-nationally so we felt a statement was prudent. 1. This is not a legal document. This is simply a statement of our commitment to our...
by Christine Thome | Apr 3, 2018 | Uncategorized
Google’s Gmail for Business Offers High False Positives Excerpted from the March 28, 2018 IRONSCALES Blog, written by Eyal Benishti Google’s Gmail for Business has had an overhaul and now claims to offer AI-powered security features. According to its marketing...
by Christine Thome | Jan 31, 2018 | Uncategorized
Excerpted from the Barracuda Blog, by Christine Barry It’s Tax Identity Theft Awareness Week in the United States, which means that tax-related identity theft happens often enough to get the government’s attention. The Federal Trade Commission...
by Christine Thome | Jan 5, 2018 | Uncategorized
Excerpted from Cylance Blog, January 4, 2018 Chip manufacturers have acknowledged a set of vulnerabilities (CVE-2017-5715, CVE-2017-5753, and CVE-2017-5754) that are exploitable at the hardware architecture level, leaving multiple operating systems impacted,...


