by Paul Comfort | Aug 17, 2018 | Cloud, Security, Storage
Many businesses are moving towards the cloud for enterprise applications. Where to store important data, however, may be problematic for some. Paul Comfort, Chi Corporation’s lead engineer, answers commonly asked questions to help you determine whether or not...
by Paul Comfort | Jul 16, 2018 | Infrastructure, mobile threats, Security
Twenty years ago, if you mentioned spam and phishing in the same sentence, one would assume you were enjoying some time on the lake and a sandwich made from canned meat. In today’s IT world, those words have much more menacing meanings (although the canned meat...
by Christine Thome | Jul 3, 2018 | mobile threats, Security
Chances are you’d be more inclined to open and act on an email from a colleague, friend or someone you know as opposed to someone you don’t. Cybercriminals know this, which is why they are sending attacks to your friends and colleagues—from your email account....
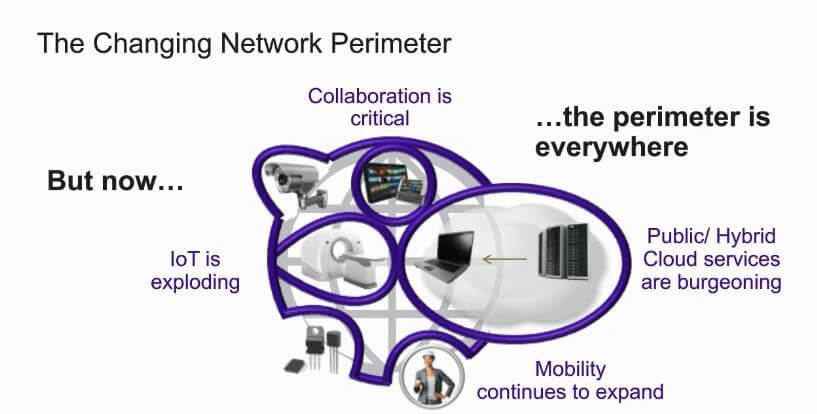
by Christine Thome | Jun 6, 2018 | Networking, Security
The digitalization of our society is happening now, uniquely and definitively transforming how organizations operate on a day-to-day basis, and opening up progressive and exciting opportunities across all industries. Some of these include: In hotel and lodging, mobile...
by Christine Thome | Jun 6, 2018 | Backup, Security, Storage
Along with most everyone rushing to update their privacy policies and reaffirm your consent, the “other” copies of your data have begun to creep into the discussion, such as a piece that appeared on The Register. Wait? What other copies?!? You know, all...
by Paul Comfort | Jun 6, 2018 | Cloud, Infrastructure, Security
Security is hard, and here is a great example as to why. I am using Amazon WorkSpaces for this example because I recently ran up against this problem, but a similar issue could happen during any cloud software product’s normal lifecycle. Amazon WorkSpaces is a...

